Microsoft (R) Windows Debugger Version 6.11.0001.404 X86
Copyright (c) Microsoft Corporation. All rights reserved.
Loading Dump File [F:\Programme\081011-13072-01.dmp]
Mini Kernel Dump File: Only registers and stack trace are available
Symbol search path is: SRV*C:\symbols*
http://msdl.microsoft.com/download/symbols
Executable search path is:
Windows 7 Kernel Version 7601 (Service Pack 1) MP (8 procs) Free x64
Product: WinNt, suite: TerminalServer SingleUserTS Personal
Built by: 7601.17640.amd64fre.win7sp1_gdr.110622-1506
Machine Name:
Kernel base = 0xfffff800`02e66000 PsLoadedModuleList = 0xfffff800`030ab670
Debug session time: Wed Aug 10 11:54:59.962 2011 (GMT+2)
System Uptime: 0 days 2:21:12.805
Loading Kernel Symbols
...............................................................
................................................................
.......................................
Loading User Symbols
Loading unloaded module list
..........
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
Use !analyze -v to get detailed debugging information.
BugCheck A, {217a, f, 1, fffff80002ecce0e}
Probably caused by : ndis.sys ( ndis!ndisMiniportMessageIsr+a8 )
Followup: MachineOwner
---------
0: kd> !analyze -v
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
IRQL_NOT_LESS_OR_EQUAL (a)
An attempt was made to access a pageable (or completely invalid) address at an
interrupt request level (IRQL) that is too high. This is usually
caused by drivers using improper addresses.
If a kernel debugger is available get the stack backtrace.
Arguments:
Arg1: 000000000000217a, memory referenced
Arg2: 000000000000000f, IRQL
Arg3: 0000000000000001, bitfield :
bit 0 : value 0 = read operation, 1 = write operation
bit 3 : value 0 = not an execute operation, 1 = execute operation (only on chips which support this level of status)
Arg4: fffff80002ecce0e, address which referenced memory
Debugging Details:
------------------
WRITE_ADDRESS: GetPointerFromAddress: unable to read from fffff80003115100
000000000000217a
CURRENT_IRQL: f
FAULTING_IP:
nt!KeInsertQueueDpc+18e
fffff800`02ecce0e 0f0d8bdc210000 prefetchw [rbx+21DCh]
CUSTOMER_CRASH_COUNT: 1
DEFAULT_BUCKET_ID: VISTA_DRIVER_FAULT
BUGCHECK_STR: 0xA
PROCESS_NAME: System
TRAP_FRAME: fffff80004acc850 -- (.trap 0xfffff80004acc850)
NOTE: The trap frame does not contain all registers.
Some register values may be zeroed or incorrect.
rax=0000000000000001 rbx=0000000000000000 rcx=fffffa800b675500
rdx=0000000000000022 rsi=0000000000000000 rdi=0000000000000000
rip=fffff80002ecce0e rsp=fffff80004acc9e0 rbp=fffffa800b675518
r8=0000000000000029 r9=0000000000000000 r10=0000000000000000
r11=fffff80003058e80 r12=0000000000000000 r13=0000000000000000
r14=0000000000000000 r15=0000000000000000
iopl=0 nv up ei pl nz na po nc
nt!KeInsertQueueDpc+0x18e:
fffff800`02ecce0e 0f0d8bdc210000 prefetchw [rbx+21DCh]
Resetting default scope
LAST_CONTROL_TRANSFER: from fffff80002ee21e9 to fffff80002ee2c40
STACK_TEXT:
fffff800`04acc708 fffff800`02ee21e9 : 00000000`0000000a 00000000`0000217a 00000000`0000000f 00000000`00000001 : nt!KeBugCheckEx
fffff800`04acc710 fffff800`02ee0e60 : fffffa80`07f44000 fffff880`06d083cd fffffa80`0c337000 fffff800`03058e80 : nt!KiBugCheckDispatch+0x69
fffff800`04acc850 fffff800`02ecce0e : 00000000`40950088 00000000`00000001 00000001`00000000 ffffda7e`39cc3a88 : nt!KiPageFault+0x260
fffff800`04acc9e0 fffff880`01cd2488 : fffffa80`0b675518 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KeInsertQueueDpc+0x18e
fffff800`04acca70 fffff800`02edea7c : fffff800`03058e80 fffffa80`00000001 00000000`00000000 00000000`00000000 : ndis!ndisMiniportMessageIsr+0xa8
fffff800`04accab0 fffff800`02eda942 : fffff800`03058e80 fffff800`00000001 00000000`00000001 fffff880`00000000 : nt!KiInterruptDispatch+0x16c
fffff800`04accc40 00000000`00000000 : fffff800`04acd000 fffff800`04ac7000 fffff800`04accc00 00000000`00000000 : nt!KiIdleLoop+0x32
STACK_COMMAND: kb
FOLLOWUP_IP:
ndis!ndisMiniportMessageIsr+a8
fffff880`01cd2488 84c0 test al,al
SYMBOL_STACK_INDEX: 4
SYMBOL_NAME: ndis!ndisMiniportMessageIsr+a8
FOLLOWUP_NAME: MachineOwner
MODULE_NAME: ndis
IMAGE_NAME: ndis.sys
DEBUG_FLR_IMAGE_TIMESTAMP: 4ce79392
FAILURE_BUCKET_ID: X64_0xA_ndis!ndisMiniportMessageIsr+a8
BUCKET_ID: X64_0xA_ndis!ndisMiniportMessageIsr+a8
Followup: MachineOwner
---------
0: kd> .trap 0xfffff80004acc850
NOTE: The trap frame does not contain all registers.
Some register values may be zeroed or incorrect.
rax=0000000000000001 rbx=0000000000000000 rcx=fffffa800b675500
rdx=0000000000000022 rsi=0000000000000000 rdi=0000000000000000
rip=fffff80002ecce0e rsp=fffff80004acc9e0 rbp=fffffa800b675518
r8=0000000000000029 r9=0000000000000000 r10=0000000000000000
r11=fffff80003058e80 r12=0000000000000000 r13=0000000000000000
r14=0000000000000000 r15=0000000000000000
iopl=0 nv up ei pl nz na po nc
nt!KeInsertQueueDpc+0x18e:
fffff800`02ecce0e 0f0d8bdc210000 prefetchw [rbx+21DCh]
0: kd> .bugcheck
Bugcheck code 0000000A
Arguments 00000000`0000217a 00000000`0000000f 00000000`00000001 fffff800`02ecce0e
0: kd> kb
*** Stack trace for last set context - .thread/.cxr resets it
RetAddr : Args to Child : Call Site
fffff880`01cd2488 : fffffa80`0b675518 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KeInsertQueueDpc+0x18e
fffff800`02edea7c : fffff800`03058e80 fffffa80`00000001 00000000`00000000 00000000`00000000 : ndis!ndisMiniportMessageIsr+0xa8
fffff800`02eda942 : fffff800`03058e80 fffff800`00000001 00000000`00000001 fffff880`00000000 : nt!KiInterruptDispatch+0x16c
00000000`00000000 : fffff800`04acd000 fffff800`04ac7000 fffff800`04accc00 00000000`00000000 : nt!KiIdleLoop+0x32
0: kd> kv
*** Stack trace for last set context - .thread/.cxr resets it
Child-SP RetAddr : Args to Child : Call Site
fffff800`04acc9e0 fffff880`01cd2488 : fffffa80`0b675518 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KeInsertQueueDpc+0x18e
fffff800`04acca70 fffff800`02edea7c : fffff800`03058e80 fffffa80`00000001 00000000`00000000 00000000`00000000 : ndis!ndisMiniportMessageIsr+0xa8
fffff800`04accab0 fffff800`02eda942 : fffff800`03058e80 fffff800`00000001 00000000`00000001 fffff880`00000000 : nt!KiInterruptDispatch+0x16c (TrapFrame @ fffff800`04accab0)
fffff800`04accc40 00000000`00000000 : fffff800`04acd000 fffff800`04ac7000 fffff800`04accc00 00000000`00000000 : nt!KiIdleLoop+0x32
0: kd> .trap fffff800`04accab0
NOTE: The trap frame does not contain all registers.
Some register values may be zeroed or incorrect.
rax=0000000000000000 rbx=0000000000000000 rcx=0000000000000002
rdx=0000000000000000 rsi=0000000000000000 rdi=0000000000000000
rip=fffff80002eda942 rsp=fffff80004accc40 rbp=0000000000000002
r8=0000000000000000 r9=0000000000000000 r10=0000000000000000
r11=fffff80003058e80 r12=0000000000000000 r13=0000000000000000
r14=0000000000000000 r15=0000000000000000
iopl=0 nv up ei ng nz na po nc
nt!KiIdleLoop+0x32:
fffff800`02eda942 440f22c1 mov cr8,rcx
0: kd> kb
*** Stack trace for last set context - .thread/.cxr resets it
RetAddr : Args to Child : Call Site
00000000`00000000 : fffff800`04acd000 fffff800`04ac7000 fffff800`04accc00 00000000`00000000 : nt!KiIdleLoop+0x32




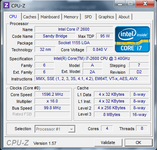
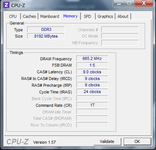
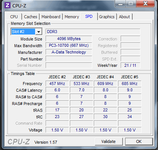
 )
)